lrk
September 16, 2024, 1:44pm
1
Hello,
Is it possible to restrict the service apply rules so that users can only see and create apply rules that are assigned to specific host groups?
If this is not possible, is it perhaps possible via service groups?
For example, how do you restrict the service apply rules for different teams?
Many thanks for your help!
rivad
September 16, 2024, 2:05pm
2
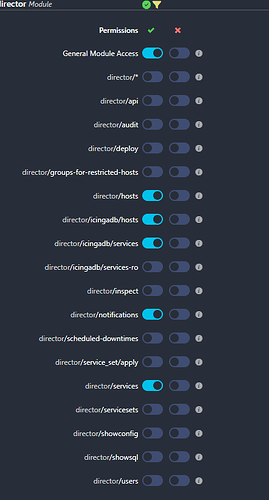
Users can see apply rules based on *director* /service/apply/filter-by-name - maybe use a team/customer prefix team a * or customer 1234 *.
Not sure, how to restrict the rule in the apply rules itself based on users/roles.
lrk
September 17, 2024, 5:14am
3
Hi @rivad
thanks for your fast reply!
I also don’t understand why there are so few options to restrict the director.
rivad
September 17, 2024, 7:19am
4
Not sure about this as I work with tags in custom vars and use them to apply service-sets.
This way my users can add the tags to the hosts and never need to deal with the apply rules.
2 Likes
lrk
September 17, 2024, 9:01am
5
That’s a cool concept, thanks for sharing your experience.
rivad
September 17, 2024, 9:07am
6
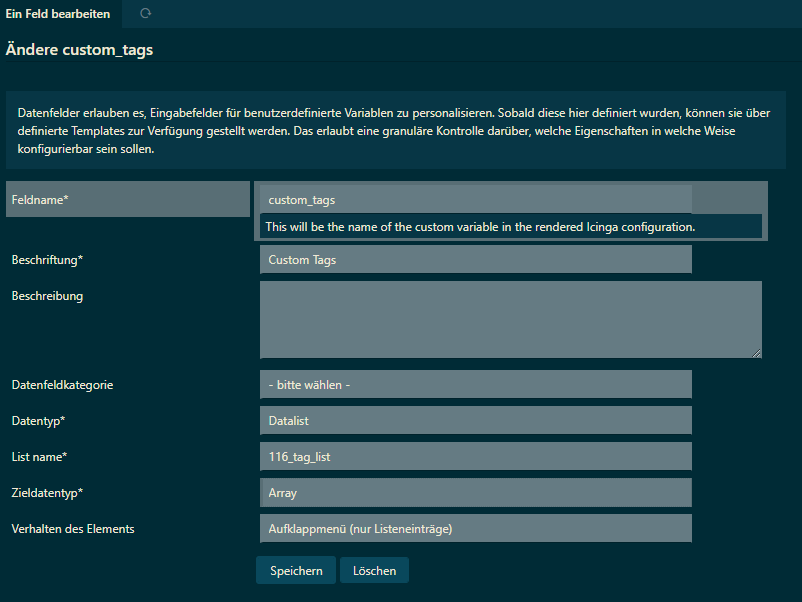
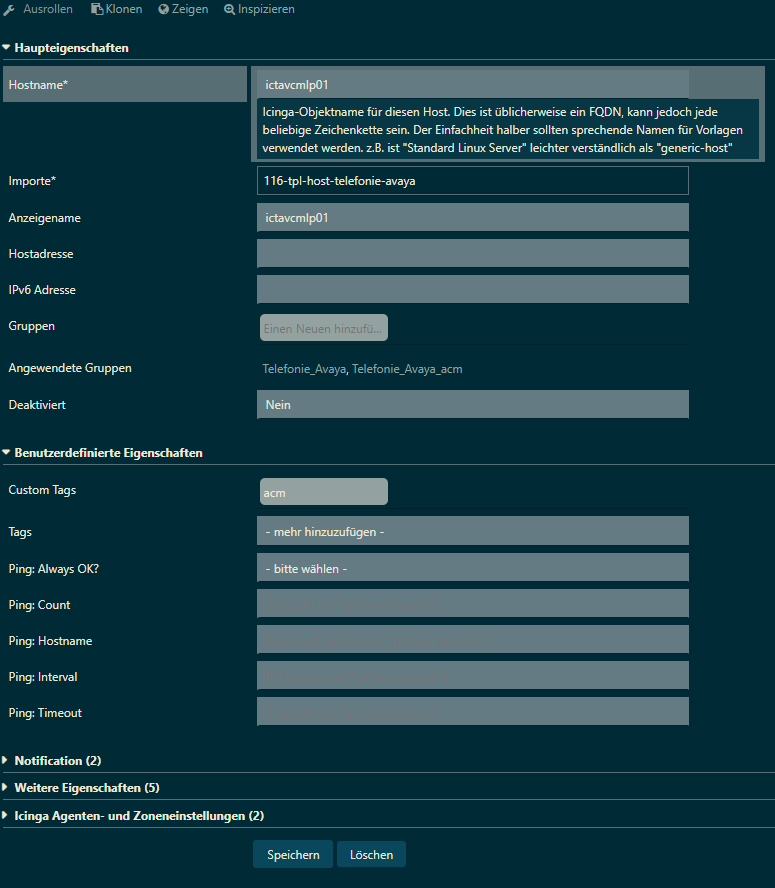
Here an example from my installation.
116 is a customer prefix you can ignore.
/icingaweb2/director/data/fields?q=tag#!/icingaweb2/director/datafield/edit?id=1292
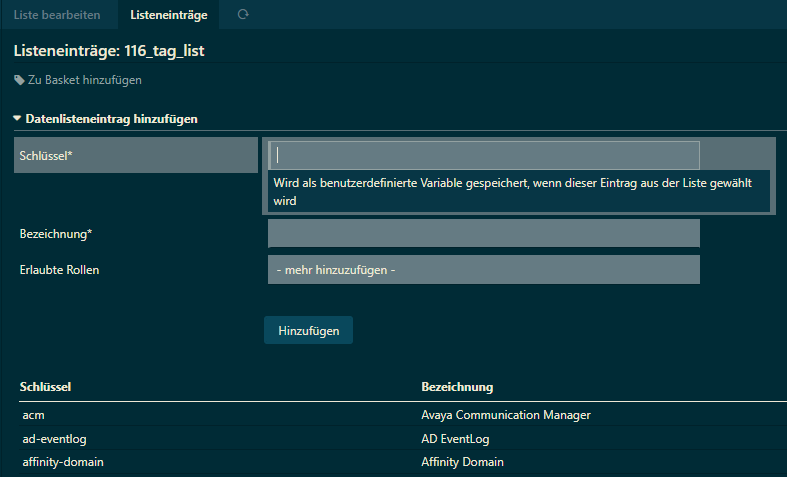
/icingaweb2/director/data/lists#!/icingaweb2/director/data/listentry?list=116_tag_list
Here you can restrict the usage of tags to allowed roles.
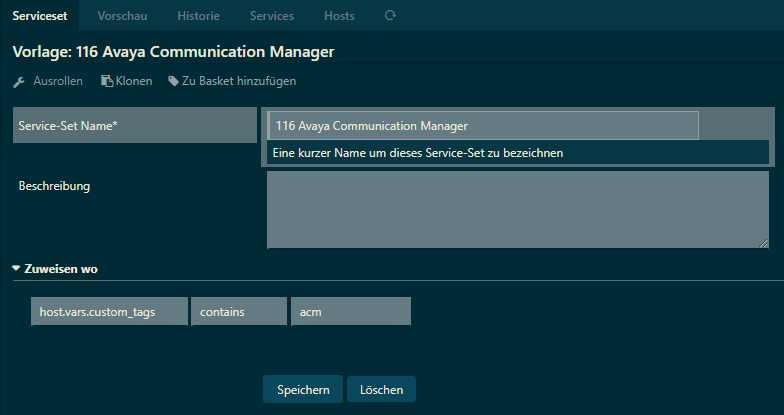
/icingaweb2/director/serviceset?uuid=a8adebab-ec51-4d43-ad1f-712756260cb3
If it doesn’t work it’s most probably not set to contains
2 Likes