This is a similar issue reported elsewhere in the message board but without any solution. My icinga2 implementation is a bit different than what I’ve seen elsewhere so I’ll include some examples.
The issue I’m experiencing is that the local output on the Windows server is working as expected, but the Icinga2 web console isn’t showing the same output.
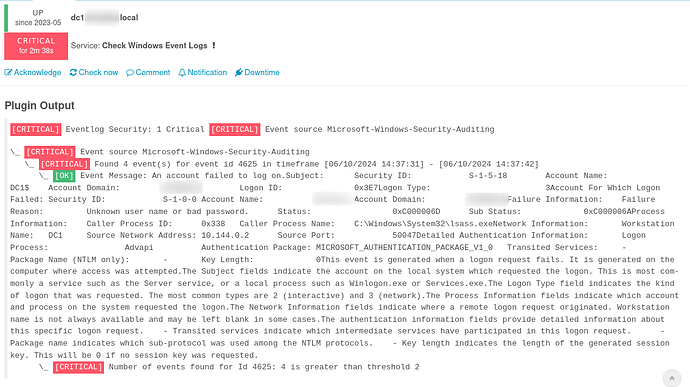
I want to check the Security log on the domain controller for event id 4625 (failed login). I’m using that event id because it’s easy to test - future additions will include more event logs. On the domain controller my test returns the expected output. I purposefully fail 3 logins at the console and invoke the command:
Invoke-IcingaCheckEventlog -LogName Security -Warning 1 -Critical 2 -Verbosity 0 -After 10m -IncludeEventId 4625
The output is returned beautifully:
[CRITICAL] Eventlog Security: 1 Critical [CRITICAL] Event source Microsoft-Windows-Security-Auditing
\_ [CRITICAL] Event source Microsoft-Windows-Security-Auditing
\_ [CRITICAL] Found 3 event(s) for event id 4625 in timeframe [06/09/2024 12:14:55] - [06/09/2024 12:15:00]
\_ [CRITICAL] Number of events found for Id 4625: 3 is greater than threshold 2
| '4625::ifw_eventlog::count'=3c;;
2
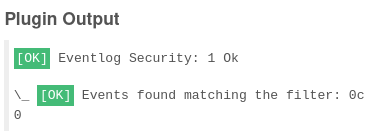
However, in the Icinga web console it never changes status. It just shows OK:
My implementation is as such (zones.d/global-templates/commands-windows.conf):
object CheckCommand "securitylogfailure" {
command = [ "C:\\Windows\\system32\\WindowsPowerShell\\v1.0\\powershell.exe" ]
arguments = {
"--command" = {
value = "& 'Invoke-IcingaCheckEventLog'"
skip_key = true
order = -7
}
"-LogName" = {
value = "'Security'"
order = -6
}
"-Warning" = {
value = 1
order = -5
}
"-Critical" = {
value = 2
order = -4
}
"-Verbosity" = {
value = 0
order = -3
}
"-After" = {
value = "'10m'"
order = -2
}
"-IncludeEventId" = {
value = 4625
order = -1
}
}
}
zones.d/global-templates/services-windows.conf:
apply Service "securitylogfailure" {
check_command = "securitylogfailure"
command_endpoint = host.address
assign where host.vars.securitylogfailure == true
}
and on the relevant host (zones.d/dc1.domain.local/dc1.domain.local):
object Host "dc1.domain.local" {
import "windows_server"
check_command = "hostalive"
address = "dc1.domain.local"
vars.agent_endpoint = name
vars.securitylogfailure = true
vars.memory = true
vars.cpu = true
vars.disks["disk"] = {
}
}
I’m sure there are more elegant ways to implement this and I’m happy to hear about them. For the context of this particular issue, though, I’d like to know if I’m implementing it correctly in the scope of my syntax. For the record, I have a bunch of other checks implemented identically which work. Or, is this an issue outside the method of implementation such as a bug in the Invoke-* command? Thanks for reading!