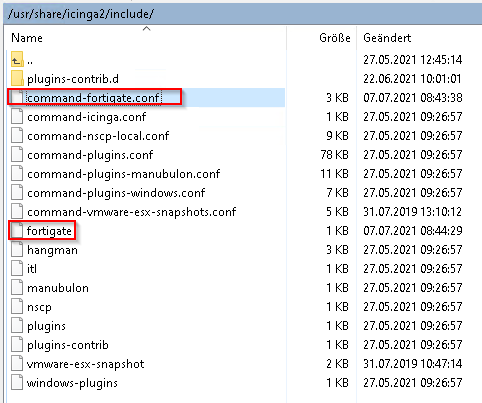
So i found this, where at the bottom it has the definition of the check command.
I put it into a file and placed it at /usr/share/inlcude
But it doesnt work. Wrong folder?
From bcaa3dd4b0309d1f46e60c7baac83bf11517a53c Mon Sep 17 00:00:00 2001
From: riskersen <oliskibbe@gmail.com>
Date: Tue, 25 Jul 2017 07:59:37 +0200
Subject: [PATCH] Add Fortinet CheckCommand definition
refs #5429
---
doc/10-icinga-template-library.md | 28 ++++++++++++
itl/plugins-contrib.d/CMakeLists.txt | 2 +-
itl/plugins-contrib.d/fortinet.conf | 86 ++++++++++++++++++++++++++++++++++++
3 files changed, 115 insertions(+), 1 deletion(-)
create mode 100644 itl/plugins-contrib.d/fortinet.conf
diff --git a/doc/10-icinga-template-library.md b/doc/10-icinga-template-library.md
index ac90f74..2c1659c 100644
--- a/doc/10-icinga-template-library.md
+++ b/doc/10-icinga-template-library.md
@@ -374,6 +374,34 @@ Name | Description
flexlm_licensefile | **Required.** Name of license file (usually license.dat).
flexlm_timeout | **Optional.** Plugin time out in seconds. Defaults to 15.
+### fortinet <a id="plugin-check-command-fortinet"></a>
+The [check_fortigate.pl] (https://github.com/riskersen/Monitoring) plugin checks Fortinet devices.
+
+This CheckCommand expects an IPv4 address.
+
+Custom attributes passed as [command parameters](03-monitoring-basics.md#command-passing-parameters):
+
+Name | Description
+-------------------------|-------------------------
+fortinet_address | **Optional.** The host's IPv4 address. Defaults to "$address$".
+fortinet_community | **Optional.** The host's SNMP community. Defaults to public
+fortinet_snmpversion | **Optional.** The host's SNMP version. Defaults to version 2 (community bsaed, v2c)
+fortinet_check | **Optional.** What to check. Defaults to status
+fortinet_snmpv3user | **Optional.** Applies for SNMPv3 only. Login user
+fortinet_snmpv3authpass | **Optional.** Applies for SNMPv3 only. Authentication password
+fortinet_snmpv3authprot | **Optional.** Applies for SNMPv3 only. Authentication protocol
+fortinet_snmpv3privpass | **Optional.** Applies for SNMPv3 only. Privacy password
+fortinet_snmpv3privprot | **Optional.** Applies for SNMPv3 only. Privacy protocol
+fortinet_serial | **Optional.** Used to check if preferred master is actually master
+fortinet_slave | **Optional.** Used to check slave node of a cluster
+fortinet_warn | **Optional.** Warning threshold. Defaults to 75, UOM depends on the check type
+fortinet_crit | **Optional.** Critical threshold. Defaults to 95, UOM depends on the check type
+fortinet_nosync | **Optional.** Exclude in sync check from cluster status check
+fortinet_vpnoutput | **Optional.** Applies for VPN check. Output-Mode: 0 => just print, 1 => print and show failed tunnel, 2 => critical
+fortinet_vpnmode | **Optional.** Applies for VPN check. VPN-Mode: both => IPSec & SSL/OpenVPN, ipsec => IPSec only, ssl => SSL/OpenVPN only"
+fortinet_vpnwhitelist | **Optional.** Applies for VPN IPSEC check. Include only entries matching a regular expression (applies before --blacklist)"
+fortinet_vpnblacklist | **Optional.** Applies for VPN IPSEC check. Include only entries matching a regular expression (applies before --blacklist)"
+fortinet_filehelper | **Optional.** Path to store helper files. Defaults to $TEMPPATH$"
### fping4 <a id="plugin-check-command-fping4"></a>
diff --git a/itl/plugins-contrib.d/CMakeLists.txt b/itl/plugins-contrib.d/CMakeLists.txt
index 27d2b7e..e56ed7b 100644
--- a/itl/plugins-contrib.d/CMakeLists.txt
+++ b/itl/plugins-contrib.d/CMakeLists.txt
@@ -16,6 +16,6 @@
# Inc., 51 Franklin St, Fifth Floor, Boston, MA 02110-1301, USA.
install(
- FILES databases.conf hardware.conf icingacli.conf ipmi.conf logmanagement.conf metrics.conf network-components.conf network-services.conf operating-system.conf raid-controller.conf smart-attributes.conf storage.conf virtualization.conf vmware.conf web.conf
+ FILES databases.conf fortinet.conf hardware.conf icingacli.conf ipmi.conf logmanagement.conf metrics.conf network-components.conf network-services.conf operating-system.conf raid-controller.conf smart-attributes.conf storage.conf virtualization.conf vmware.conf web.conf
DESTINATION ${CMAKE_INSTALL_DATADIR}/icinga2/include/plugins-contrib.d
)
diff --git a/itl/plugins-contrib.d/fortinet.conf b/itl/plugins-contrib.d/fortinet.conf
new file mode 100644
index 0000000..7efe246
--- /dev/null
+++ b/itl/plugins-contrib.d/fortinet.conf
@@ -0,0 +1,86 @@
+object CheckCommand "fortinet" {
+ command = [ PluginDir + "/check_fortigate.pl" ]
+
+ arguments = {
+ "-H" = {
+ value = "$fortinet_address$"
+ required = true
+ }
+ "-C" = "$fortinet_community$"
+ "-v" = "$fortinet_snmpversion$"
+ "-T" = {
+ value = "$fortinet_check$"
+ description = "CPU, network, Memory, Cluster, Sessions, VPN, Disk-Space. Consult help output if more info needed!"
+ }
+ "-U" = {
+ set_if = "$fortinet_snmpv3user$"
+ description = "SNMPv3 Auth user"
+ }
+ "-A" = {
+ set_if = "$fortinet_snmpv3authpass$"
+ description = "SNMPv3 Auth password"
+ }
+ "-a" = {
+ set_if = "$fortinet_snmpv3authprot$"
+ description = "SNMPv3 Auth protocol (defaults to SHA)"
+ }
+ "-X" = {
+ set_if = "$fortinet_snmpv3privpass$"
+ description = "SNMPv3 Priv password"
+ }
+ "-x" = {
+ set_if = "$fortinet_snmpv3privprot$"
+ description = "SNMPv3 Priv protocol (defaults to AES)"
+ }
+ "-S" = {
+ set_if = "$fortinet_serial$"
+ description = "Serial number for identification of primary master"
+ }
+ "-s" = {
+ set_if = "$fortinet_slave$"
+ description = "Check on slave OIDs, please use dedicated mgmt interface or SNMP community by appending serial number to community"
+ }
+ "-w" = {
+ value = "$fortinet_warn$"
+ description = "Warning threshold, applies to cpu, mem, session, fazcpu, fazmem, fazdisk"
+ }
+ "-c" = {
+ value = "$fortinet_crit$"
+ description = "Critical threshold, applies to cpu, mem, session, fazcpu, fazmem, fazdisk"
+ }
+ "-n" = {
+ set_if = "$fortinet_nosync$"
+ description = "Exclude cluster synchronisation check (cluster only)"
+ }
+ "-M" = {
+ set_if = "$fortinet_vpnoutput$"
+ value = "$fortinet_vpnoutput$"
+ description = "Output-Mode: 0 => just print, 1 => print and show failed tunnel, 2 => critical"
+ }
+ "-V" = {
+ set_if = "$fortinet_vpnmode$"
+ value = "$fortinet_vpnmode$"
+ description = "VPN-Mode: both => IPSec & SSL/OpenVPN, ipsec => IPSec only, ssl => SSL/OpenVPN only"
+ }
+ "-W" = {
+ value = "$fortinet_vpnwhitelist$"
+ description = "Include only entries matching a regular expression (applies before --blacklist) / IPSEC only"
+ }
+ "-B" = {
+ value = "$fortinet_vpnblacklist$"
+ description = "Exclude entries matching a regular expression (applies after --whitelist) / IPSEC only"
+ }
+ "-p" = {
+ value = "$fortinet_filehelper$"
+ description = "Path to store helper files"
+ }
+ }
+
+ vars.fortinet_address = "$address$"
+ vars.fortinet_filehelper = "$TEMPPATH$"
+ vars.fortinet_warn = "75"
+ vars.fortinet_crit = "90"
+ vars.fortinet_community = "public"
+ vars.fortinet_snmpversion = "2"
+}
+
--
1.8.3.1
Thanks already