Hello Carsten
I am working on it from director perspective
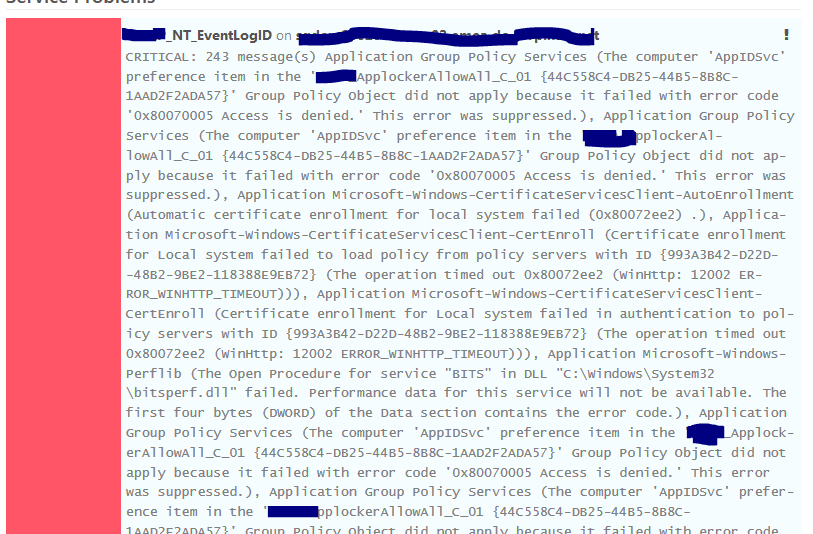
I will post screenshot of the same and then probably I will need a little bit more help to exactly try for our monitoring based on eventID
This is how it looks in the Inspect Screen:
‘C:\Program Files\NSClient++\nscp.exe’ ‘client’ ‘–log’ ‘critical’ ‘–module’ ‘CheckEventlog’ ‘-b’ ‘-q’ ‘check_eventlog’
So looks like it is listing all Critical alerts 
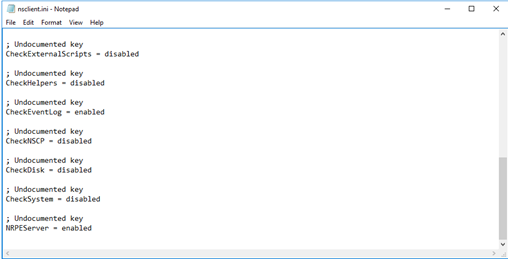
Now I need to help to monitor only very specific Event ID on a Specific source
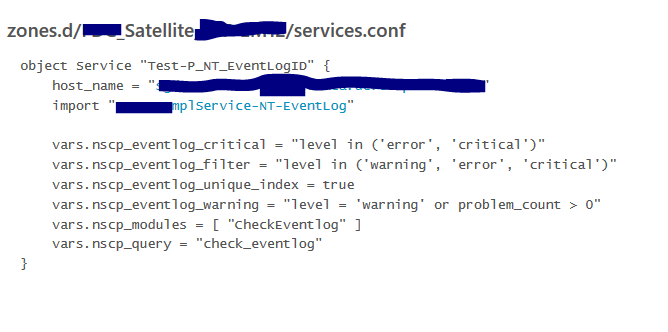
EDIT:
I added the parameter nscp_eventlog_scan_range = -10m thinking that it will clear the alert if there is no error log and the number of error patterns discovered will be less. But it doesn’t look like it has any effect on the alert. Infact what is strange the Inspect command is returning the same command
‘C:\Program Files\NSClient++\nscp.exe’ ‘client’ ‘–log’ ‘critical’ ‘–module’ ‘CheckEventlog’ ‘-b’ ‘-q’ ‘check_eventlog’
EDIT 2:
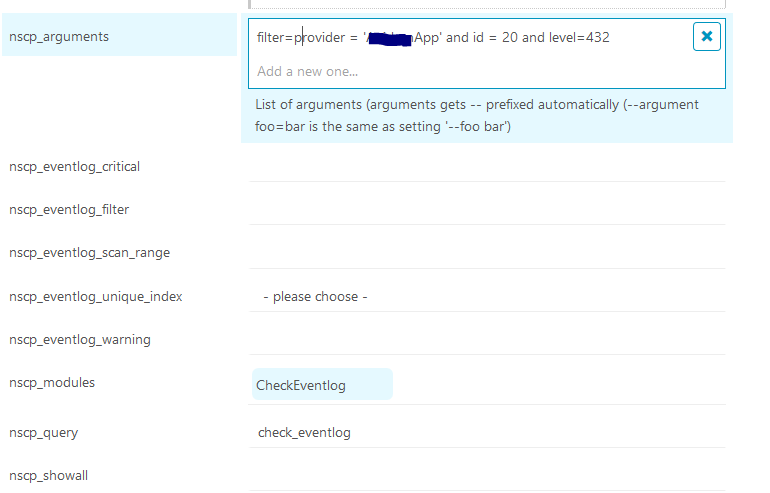
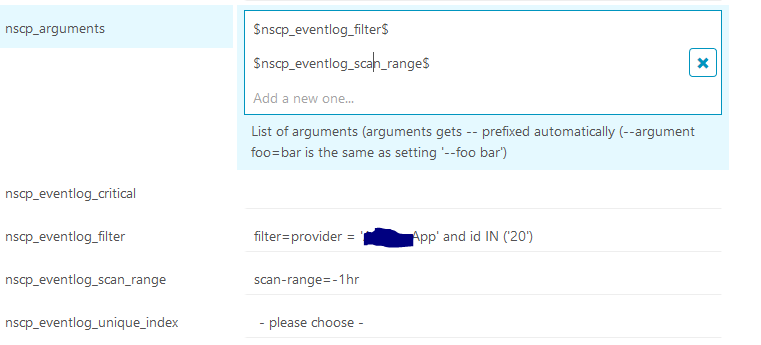
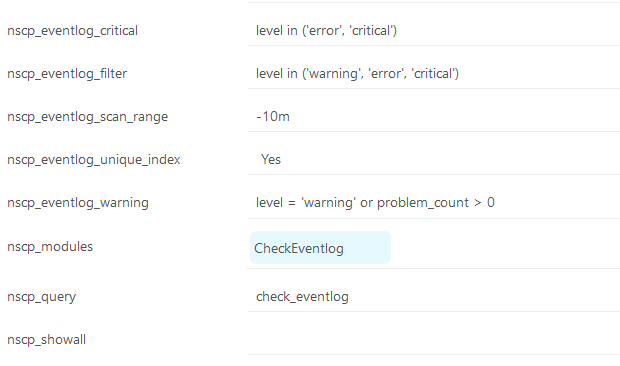
I made further changes to the service. I have added the filter like below
Now the inspect looks like below
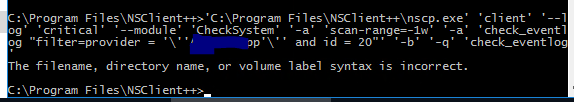
‘C:\Program Files\NSClient++\nscp.exe’ ‘client’ ‘–log’ ‘critical’ ‘–module’ ‘CheckEventlog’ ‘-a’ ‘filter=provider = ‘'’******App’'’ and id = 20 and level=432’ ‘-b’ ‘-q’ ‘check_eventlog’
This is based on the document https://docs.nsclient.org/reference/windows/CheckEventLog/
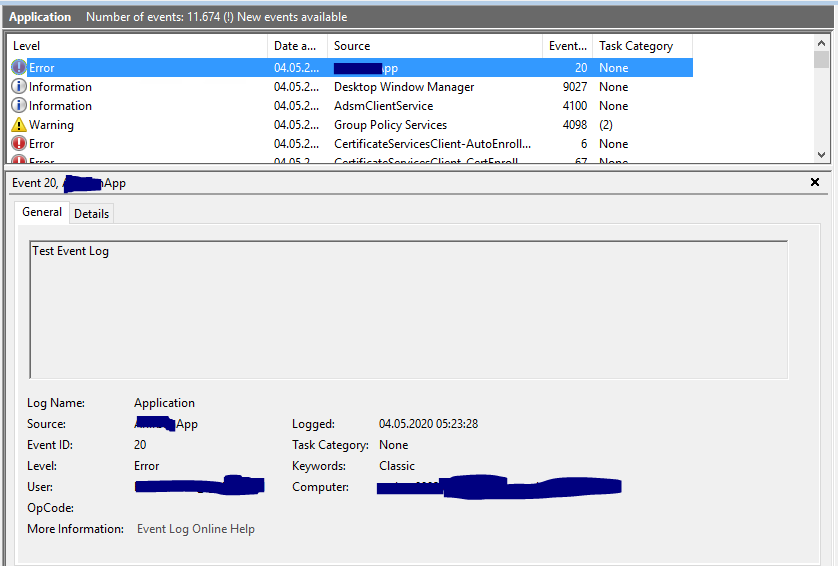
I use eventcreate to fire a event in logs
eventcreate /ID 20 /L application /T ERROR /SO ******App /D “Test Event Log”
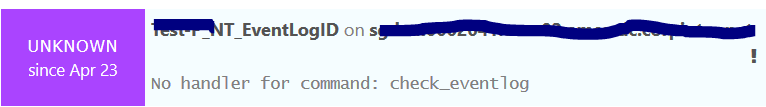
The alert won’t fire - I can see it in the event log
I am really now at my wits end. No clue how to make it work. I really need help as we are trying to establish iCinga The Monitoring Platform and I am really not able to figure this out
EDIT 3
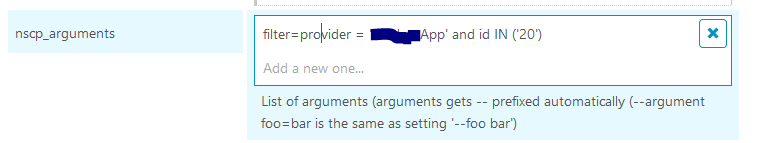
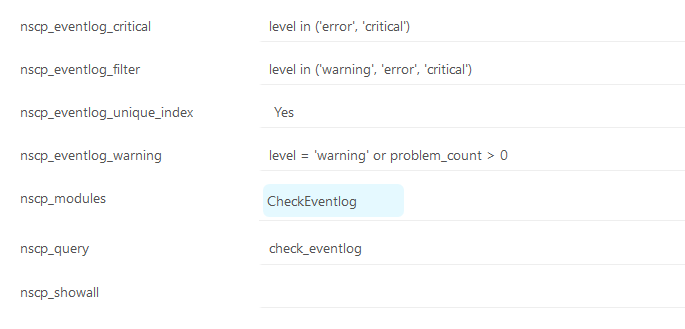
I am very close now  The stupid ID filter is suppose to be like below
The stupid ID filter is suppose to be like below
I have now 3 very pointed questions
- How can I use detail-syntax (I want to showcase the event ID in the message) I want to put “detail-syntax=%(source) %(level) ID %(id)”. How do I include it in the nscp-local command ?
- I want to filter for all levels if I use error or warning or information
- How to include scan-range=-1hr
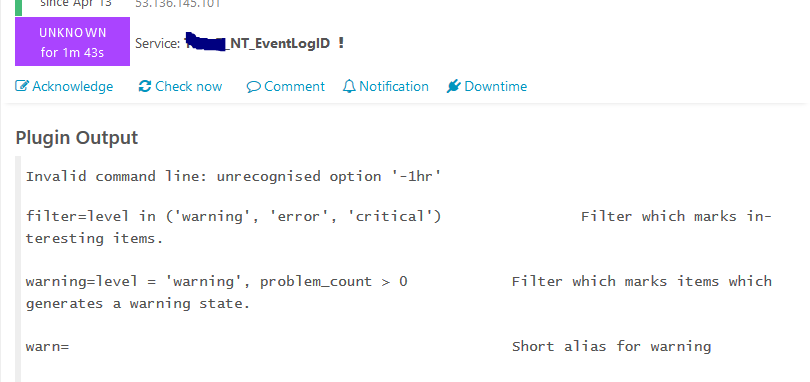
I tried the scan-range = -1hr
I am getting the below
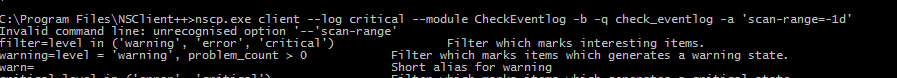
Inspect looks like below
‘C:\Program Files\NSClient++\nscp.exe’ ‘client’ ‘–log’ ‘critical’ ‘–module’ ‘CheckEventlog’ ‘-a’ ‘filter=provider = ‘'’***App’'’ and id IN (‘'‘20’'’)’ ‘-a’ ‘scan-range=-1hr’ ‘-b’ ‘-q’ ‘check_eventlog’