Dear swarm intelligence,
I am right now to setup a new Icinga2 environment for a customer that brings a new layer of compellability. In the past, I set up some environments with multi zones and satellites. So, I thought we could continue with this idea on the current project.
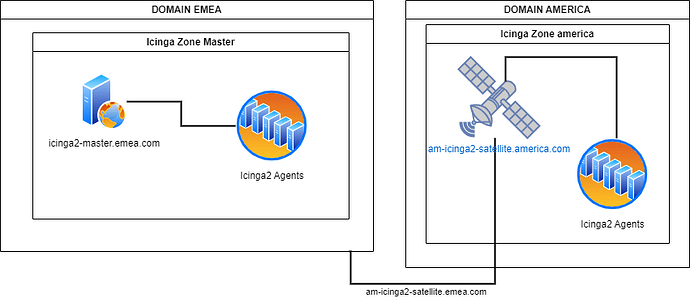
On this setup, we have the challenge that the zones have also different domain names. An example picture here:
So, we set up the master node with the “icinga2 node wizard”, setup DB, WEB, Director… the master zone works as expected, same zone same domain. Auto CSR works!
Now we tried to setup the satellite and configure also an agent behind.
Since we habe a satellite that have an interface inside each domain, we tried this setup:
satellite node setup
icinga2 node setup \
--zone am-icinga2-satellite.america.com \
--endpoint icinga2-master.emea.com \
--ticket 374c5093dbcee2c593411a2319e85c5ac4059f85 \
--cn am-icinga2-satellite.america.com \
--parent_host icinga2-master.emea.com \
--parent_zone master \
--trusted /var/lib/icinga2/certs/trusted-parent.crt \
--accept-config --accept-commands --listen "0.0.0.0,5665"
satellite zones.conf
object Endpoint "icinga2-master.emea.com" {
}
object Zone "master" {
endpoints = [ "icinga2-master.emea.com" ]
}
object Endpoint "am-icinga2-satellite.emea.com" {
}
object Zone "am-icinga2-satellite.america.com" {
endpoints = [ "am-icinga2-satellite.emea.com" ]
parent = "master"
}
object Zone "global-templates" {
global = true
}
object Zone "director-global" {
global = true
}
We put the same ticketsalt and api users from the master to the satellite.
Next Step: try to setup an agent behind the satellite inside the america zone.
Ticket was able to be retrieved from satellite, but node setup did not end as expected.
icinga agent setup syslog in america domain/zone:
"icinga2" "node" "setup" \
"--zone" "syslog.america.com" \
"--endpoint" "am-icinga2-satellite.america.com" \
"--ticket" "c816642c3b48e7ab4c65c5a20dd38737c06be866" \
"--cn" "syslog.america.com" \
"--parent_host" "am-icinga2-satellite.america.com" \
"--parent_zone" "america" \
"--trusted" "/var/lib/icinga2/certs/trusted-parent.crt" \
"--accept-config" "--accept-commands" "--listen" "0.0.0.0,5665"
In the output I can see this
Certificate request for CN 'syslog.america.com' is pending. Waiting for approval from the parent Icinga instance.",
On the satellite debug log it shows this:
information/JsonRpcConnection: Received certificate request for CN 'syslog.america.com' which couldn't be verified: self-signed certificate (code 18)
information/JsonRpcConnection: Certificate request for CN 'syslog.america.com' is pending. Waiting for approval.
warning/JsonRpcConnection: API client disconnected for identity 'syslog.america.com'
notice/ApiListener: Relaying 'pki::RequestCertificate' message
debug/JsonRpcConnection: Error while reading JSON-RPC message for identity 'syslog.america.com': Error: Operation canceled
Stacktrace:
0# __cxa_throw in /usr/lib64/icinga2/sbin/icinga2
1# 0x00000000005C8902 in /usr/lib64/icinga2/sbin/icinga2
2# icinga::JsonRpcConnection::HandleIncomingMessages(boost::asio::basic_yield_context<boost::asio::executor_binder<void (*)(), boost::asio::executor> >) in /usr/lib64/icinga2/sbin/icinga2
3# 0x0000000000864EA0 in /usr/lib64/icinga2/sbin/icinga2
4# 0x00000000008A1932 in /usr/lib64/icinga2/sbin/icinga2
5# make_fcontext in /lib64/libboost_context.so.1.75.0
We are not sure if we run into a bug, an configuration problem or that the CA Proxy do not work generally in multi domain setup. Since I know there are some Icinga2 customers out there running global setups, I am wondering if they run an own PKI or found a solution for such an environment.
Any help is appreciated!
Github Issue: https://github.com/Icinga/icinga2/issues/10024
- Version used (
icinga2 --version): r2.14.2-1 - Operating System and version: Rocky Linux release 9.3 (Blue Onyx)
- Enabled features (
icinga2 feature list): api checker command debuglog icingadb mainlog notification